CYBER SAFE
Sophisticated cyberattacks on hospitals, data centers and other critical services could spread far and wide without cybersecurity researchers keeping ahead of the threats.

HOW A SINGLE
CLICK CAN
SUMMON A
CYBER STORM
An ordinary Monday dawns, and a national power company employee is scrolling through their inbox. They click on a file link in an email from their boss, asking them to check on a minor fault reported over the weekend at one of their regional power stations. Not an unusual occurrence, so the employee suspects nothing. But this single click unwittingly triggers a cascade that, within hours, has the local area on its knees.
“From a cybersecurity perspective, all devices and employees within any given company are authentic threats, even if it occurs without harmful intent,” saysCharalambos Konstantinou, a cybersecurity researcher at KAUST.
Konstantinou researches and develops cybersecurity solutions for multiple industries, including the energy sector. His key goal is to create resilient and robust security networks that can prevent cyberattacks from crippling key infrastructures and to mitigate the knock-on effects of such attacks.
“Cybersecurity has come a long way in recent years, and experts have moved away from focusing only on detection and prevention,” he adds. “The key now is building resilience and recovery into all systems.”
FROM EMAIL TO EMERGENCY
Emails and hyperlinks embedded with computer viruses, malware and ransomware are an established method to extract money, steal data or exert power over people, com- panies and governments. However, such attacks are increasingly sophisticated. Take “spear phishing,” for example, which targets specific individuals in crucial jobs.
Returning to the example employee above: they received a bespoke email because they were in charge of a critical part of the electricity supply grid. When they opened the link in the email, the malware remotely switched off key parts of a par- ticular power station, handing the attackers some control over the grid.
During the power outage, the company’s call center is inundated with complaints from the public, enabling the company to monitor the extent of the outage. However, all is not as it seems – the attackers are flooding the company’s phone lines, so it takes hours to disentangle the scale of the attack. Mean- while, the country’s infrastructure, from transport to trade, is hugely disrupted.
BUILDING RESILIENCE
Developers now add layers of security that ensure against one individual making a mis- take. For instance, now it would be rare for one person to have the security keys for a whole power station held on their company computer. The system should impose layered decisions that requires multiple people to access a specific controlling element.
Developers are building backup solutions to ensure continuity during an attack, keeping key elements of infrastructure running locally while the attack is neutralized. One such solution is using microgrids, about which Konstantinou is a leading expert.
“Microgrids act like ‘islands’ in a storm – they provide and maintain local supply on an isolated system to keep power and communications running in the event of an attack on the main systems,” explains Konstantinou. “Microgrids can disconnect from the main power grid and operate indepen- dently. This is essential for hospitals, as they need a constant source of power to operate life-saving equipment.”
Microgrids are valuable in remote settings or in regions prone to natural disasters. In the event of an outage, the hospital microgrid would still run until the main grid is restored.
ATTACKS THAT RISK LIVES
Most industrial processes are now operated by computers and are vulnerable to cyberattacks that could risk human lives. An example is an attack that directly targets the programmable logic controllers (PLC) that are used in industrial systems to control specific processes, such as safe salinity levels in drinking water. An attack that interferes with that PLC in a water treatment plant is a risk to public health.
In industrial plants, such as petrochemical and power-generation plants, PLCs are used to control various processes and equipment, and can be programmed to detect faults, abnormal conditions or safety hazards. They can trigger appropriate emergency responses, such as activating alarms, shutting down equipment or initiating safety protocols. Under a cyberattack on the PLC, the emergency system, for example, might not work, damaging equipment as well as risking lives both inside and outside the plant. Meanwhile, a cyberattack that knocks out energy supplies even just two or three power stations can quickly ripple out- wards to cause problems across a nation’s networks, including transportation, industry and ultimately the whole economy.
The energy sector in Saudi Arabia is a prime target. The country is one of the top oil producing countries globally. It is also looking to become a world-leader in green energy, with an ambitious plan to generate 50 per- cent of electricity from renewables by 2030. Enhanced cybersecurity for both the renew- able and oil sectors in Saudi Arabia is vital.
“The rapid increase in renewable energy rollout in recent years has meant that consist- ent, robust cybersecurity measures have not been implemented in full,” says Konstantinou. “Enforcing standards and government regula- tory policies for the cybersecurity of renewables is still in the early stages, as is the case for the renewables industry across the world.”
There is an added element of risk stem- ming from solar panels on domestic buildings. In this case, the consumer of electricity is sometimes also a provider to the grid, or a “prosumer.” This means the cybersecurity layers have to flow both ways, protecting both consumers and providers.
SECURING BORDERS IN CYBERSPACE
Could the fictitious power company employ- ee’s innocent click have ramifications beyond their country and across the globe?
“Building secure barriers across national borders is a complex challenge,” says Kon- stantinou. “Channels must remain open to maintain a flow of data for international trade so the security needs to be built in. This ties into freedom of information and free speech, on which every country has dif- ferent laws and regulations.”
It is easier if governments are willing to cooperate, notes Konstantinou, because an open and secure system needs to have com- mon standards. Countries must also be willing to share threat details. Free flow of low-risk data should be allowed at all times, while sensitive data must be kept more secure.
“Transparency from the government to the public is vital. People need to trust that their personal data is handled in a secure way,” says Konstantinou.
FUTURE THREATS FROM AI
Lastly, we have to imagine an attack that learns from a target’s behavior and responses, then improves itself until it is far more danger- ous and challenging to detect. The use of arti- ficial intelligence in cyberattacks is increasing as AI technology advances further.
“AI is a double-edged sword,” says Konstantinou. “It opens doors to sophisticated security possibilities, but also means that attacks become ever more targeted and evasive, a rapidly evolving game of cat and mouse.”
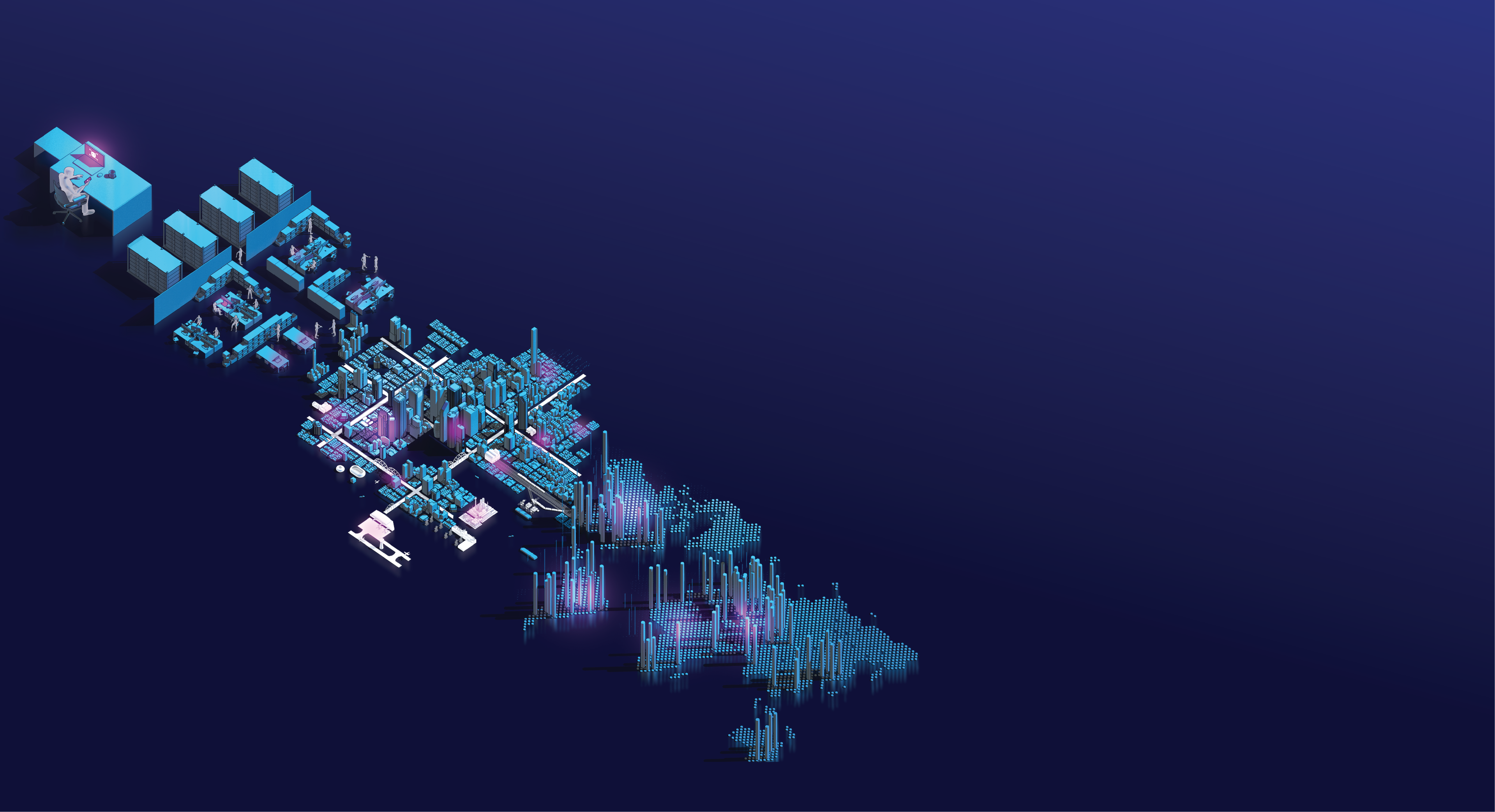

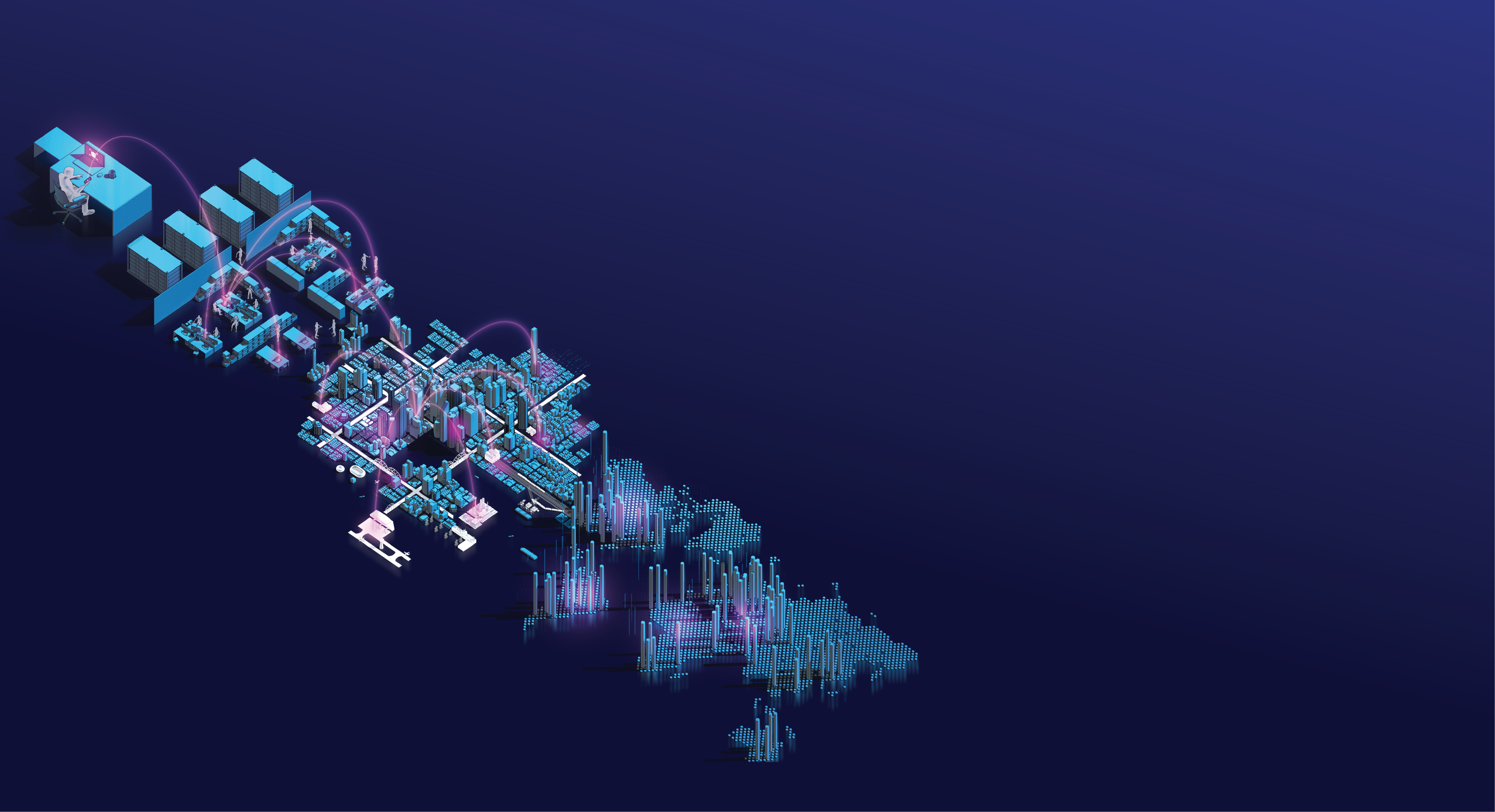
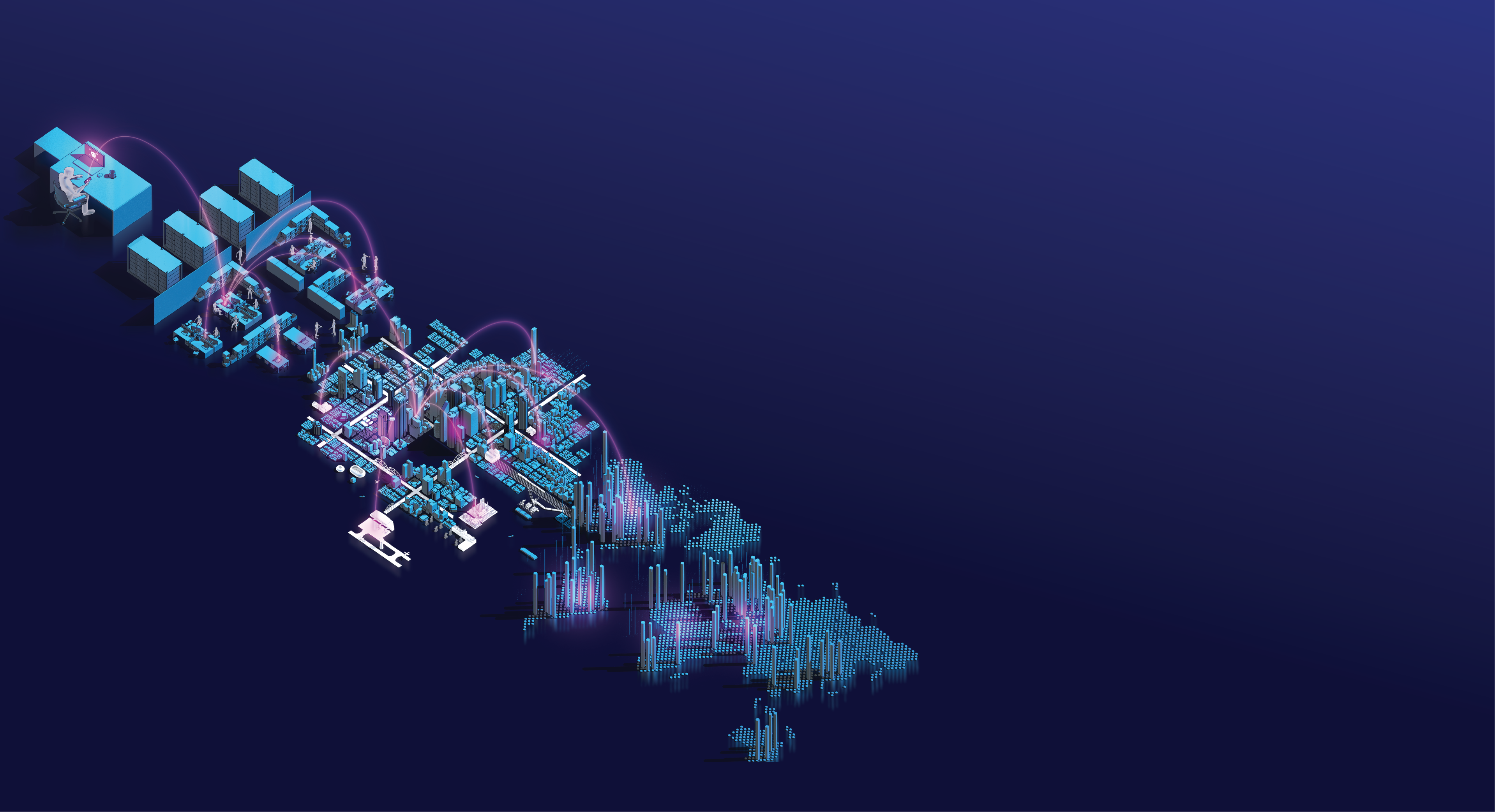
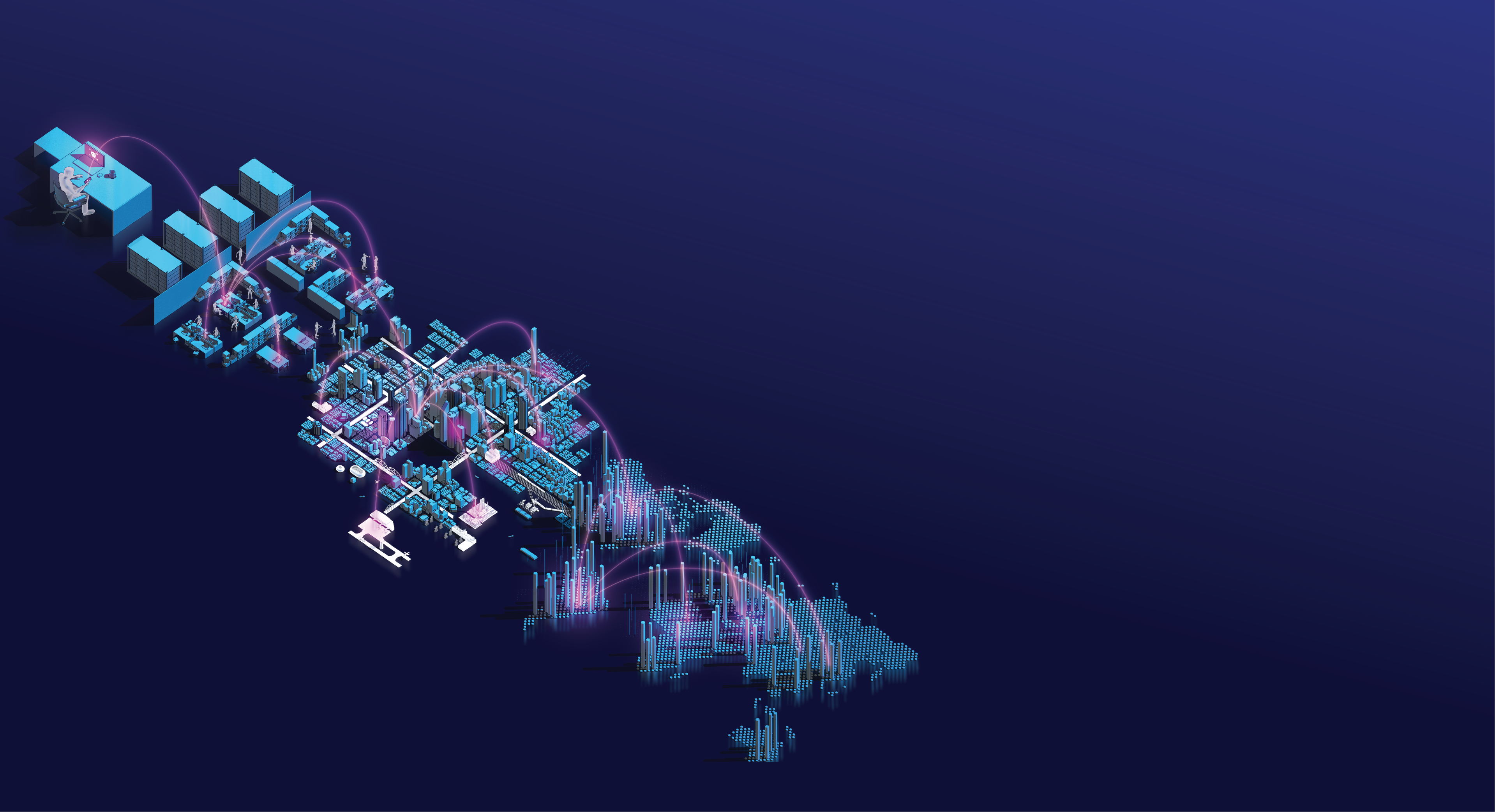
Defending Data City
Data and IT infrastructure can be imagined as a fortress city surrounded by physical barriers to protect it from outside attacks.
Within these physical barriers are patrols that seek out vulnerabilities and threats.
They react where the barriers have been breached.
Data City communicates with the outside world (the internet) via connections which can be imagined as roads were data circulates.
However, the internet also offers easy access to threats if it is not sufficiently protected.
Cyber threats include a broad spectrum of malicious activities that seek to damage, steal or prevent access to data or infrastructure.
These threats try to exploit vulnerabilities in the system to gain access to the inside of Data City.
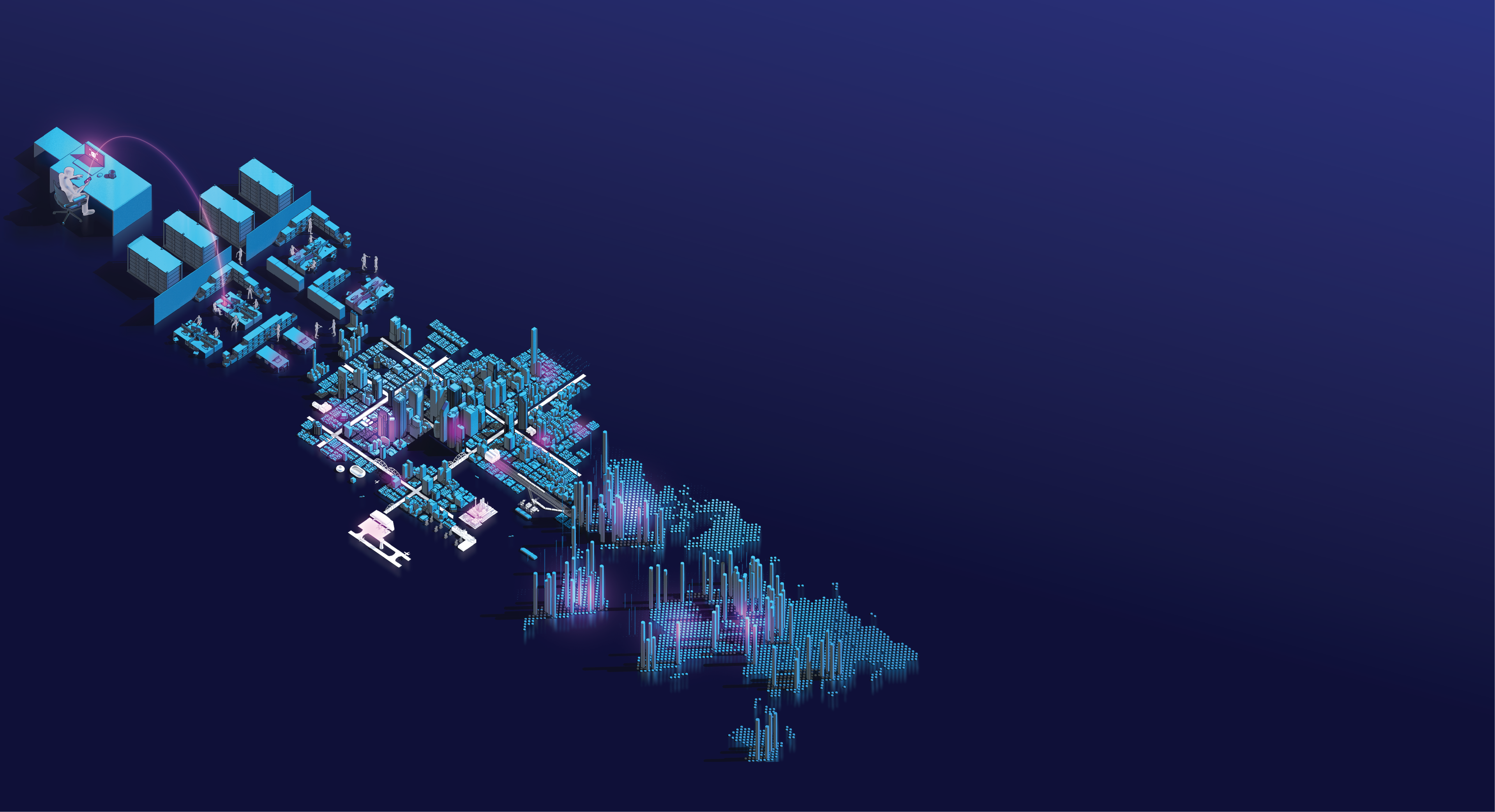
A layered defense
The primary defense system agains these threats is the firewall.
Firewalls only allow certain trusted types of authorized traffic pass through its gates. However, firewalls do not carry out comprehensive checks of the traffic passing through.
Additional monitoring is performed by the outer perimeter guards. They act as border guards that patrol and monitor incoming traffic.
The IDS guards (Intrusion Detection System) are like watchtowers, monitoring and recording all activity and raising the alarm if suspicious or malicious activity is detected.
The IPS guards (Intrusion Prevention System) detect and stop traffic that appears suspicious or malicious.
A second firewall provides added protection through tighter identity checks to prevent unauthorized access.
Meanwhile, the city is patrolled by EDR guards (Endpoint Detection and Response system) that protects Data City's infrastructure.
EDR guards can detect and stop threats and identify areas of the network that are under attack.
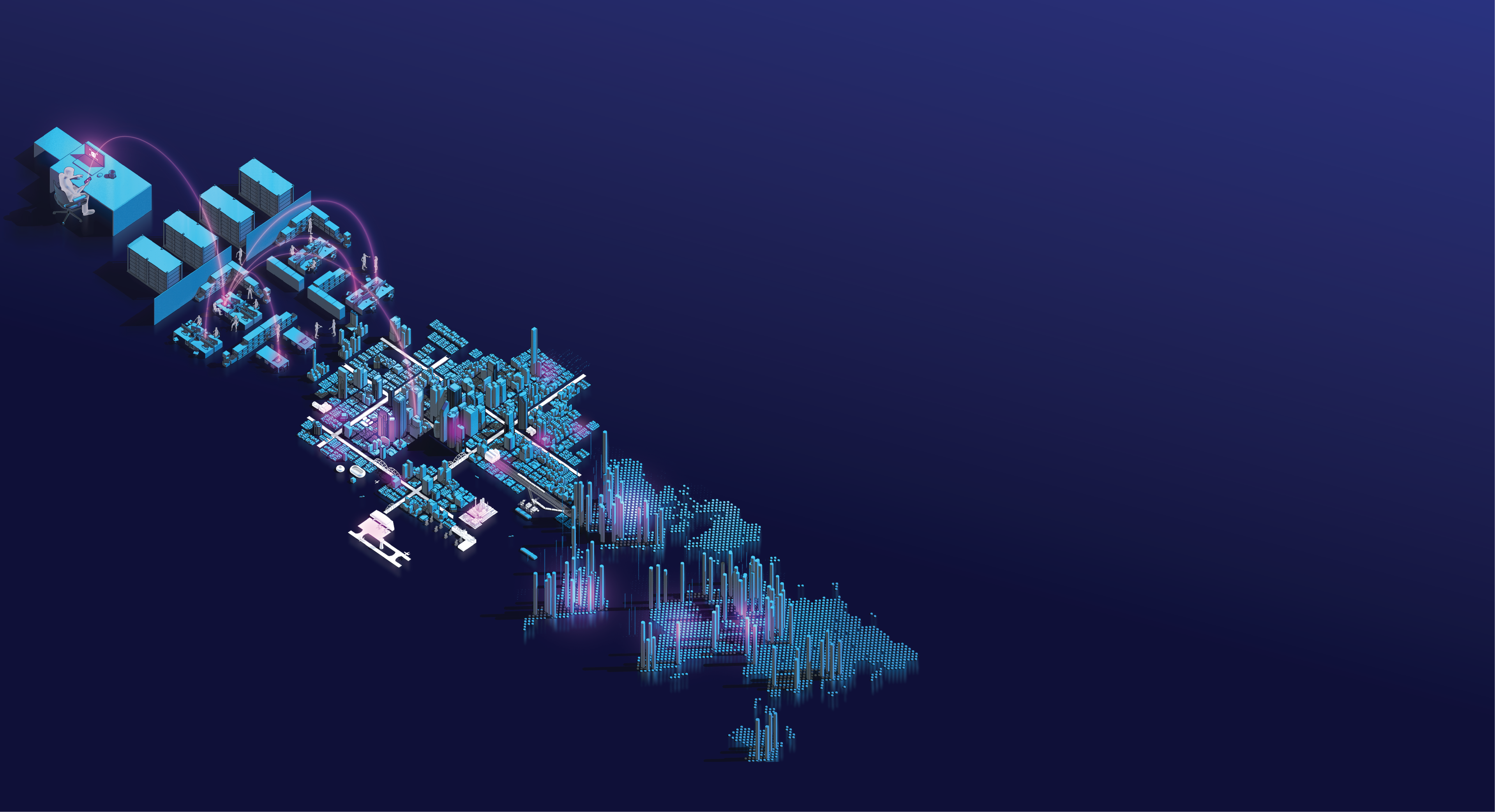
Control Center
Coordinating all cyber security aspects of Data City is the Security Operation Center (SOC).
All the information collected by the patrolling guards is reported back to the control center, where it is stored and analyzed. The SOC uses this information to decide how to respond to a threat or attack.
Last but not least, it's up to the patching teams to fix the vulnerabilities as they are discovered.
This prevents further similar attacks.
Resilience
The deployment of cyber security systems keeps Data City safe. Even when an attack is able to breach security, the systems allows the city to successfully coordinate to tolerate the failure and mount a recovery plan.
This ensures that Data City can continue functioning normally, even while under constant attack.
The field of cybersecurity is currently undergoing a period of significant flux due to the rapidly developing technology of AI. Cybersecurity experts will no longer be contending with fellow humans trying to hack or access private systems and data. The threat of AI being used to exploit weaknesses in security systems may prove to be a challenge many of us are unprepared for.
The cybersecurity systems we have used relatively successfully until now will be no match for the potential AI-generated cyber threats that will inevitably appear. The question is: are we prepared?
Art and Design: Xavier Pita, Ivan Gromicho, Heno Huang, Research Communication. Scientific review: Ali Shoker, Resilient Computing and Cybersecurity Center